- December 25, 2023
- Posted by: Jacky Melek
- Categories: Maintenance & Support, Software Development, Mobile App Development

Securing mobile applications has become crucial in contemporary software development. This importance is clear-cut: as mobile devices have seamlessly woven into our daily routines, they store a wealth of personal information, from photos and email access to social media credentials and financial details. Consequently, developers must prioritize robust security protocols to safeguard this sensitive data.
What Is Mobile App Security?
Within the realm of mobile applications, security encompasses a distinct collection of protocols, guidelines, and methodologies. While some of these are universally applicable across all devices and platforms, others are tailored expressly for mobile devices, capitalizing on their distinct attributes like cameras, diverse sensors, GPS capabilities, and more.
These mobile-centric security measures aim to shield both the device’s hardware and software from unauthorized breaches, data breaches, and assorted vulnerabilities.
Common Types of Mobile Security Threats
Given the intrinsic value and deeply personal nature of the data stored on mobile devices, they have emerged as prime targets for various malicious actors. In today’s landscape, the data accessible via smartphones often outweighs the monetary value of the devices themselves.
Typically, mobile platforms maintain user sessions even when the device is inactive or locked. This continuity spans across a myriad of applications found on smartphones and tablets, encompassing email platforms, social media apps, messaging services, streaming platforms, e-commerce portals, and more.
Should a perpetrator successfully bypass the device’s security measures, the repercussions can be severe. The compromised data might be leveraged for identity theft, extortion, reputational damage, or unauthorized financial transactions.
Additionally, scenarios where individuals misplace their devices and opportunists seize them further escalate the risk. Furthermore, data breaches can occur even without direct device theft; malicious software might clandestinely siphon off sensitive information to remote attackers.
In the cybersecurity lexicon, threats are often categorized based on their modus operandi or objectives. A foundational distinction lies between passive and active threats.
Passive threats manifest as inherent weaknesses within the codebase of mobile applications or the underlying operating system.
These vulnerabilities serve as potential gateways for unauthorized access. For instance, an application transmitting data without the safeguard of encryption or relying on antiquated security protocols exposes users to potential risks.
On the other hand, active threats represent the tools and tactics employed by cyber adversaries. This includes malware, spyware, viruses, deceptive phishing websites, and malicious scripts.
Such elements are adept at circumventing mobile defenses, often masquerading as benign applications or online platforms. Once embedded, they can operate surreptitiously, exfiltrating personal data over extended periods.
The Importance of Security in Mobile Applications
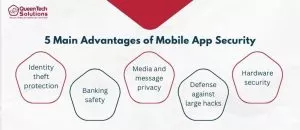
- Mobile app developers aim to prevent identity theft by safeguarding personal data, including IDs, social security numbers, and account passwords. By adhering to the latest security standards, these apps thwart unauthorized access to data stored on devices or in the cloud, ensuring that two-step verifications remain effective.
- Protecting banking details is paramount, as many apps store credit card info and addresses. If security is compromised, apps like taxi services or online shops could inadvertently expose sensitive payment data. Rigorous Quality Assurance practices minimize such risks.
- Security measures also bolster the privacy of personal media and messages. With the risk of leaked photos or messages leading to blackmail or embarrassment, encrypted communications and hidden media files deter unauthorized access.
- The importance of robust security is evident in the face of massive online breaches affecting corporations worldwide. These breaches often go unnoticed by users initially, with compromised data sold on the Darknet, leading to targeted scams and phishing attacks. Apps adhering to stringent security protocols are less vulnerable to such breaches.
- Additionally, as mobile devices advance with sophisticated sensors and AI capabilities, they pose risks if hijacked. Such devices can relay sensitive audio, video, and location data. Furthermore, malware-infected devices can join malicious botnets or be exploited for activities like cryptocurrency mining. App security protocols detect and counteract such threats, ensuring user safety.
In essence, secure mobile app development prioritizes user safety by thwarting various threats. Apps built with up-to-date security measures resonate more with users, who prioritize both physical safety and data privacy.
Ways to Improve Security in Mobile Application Development
Mobile app security is a dynamic field that continually evolves in response to the advancing tactics of hackers. As these threats grow more sophisticated, the software development community must adapt, incorporating updated standards and methodologies into their development processes.
Adhering to established guidelines and meeting standard requirements is paramount for ensuring app security.
One of the most recognized benchmarks in mobile app security is set by the Open Worldwide Application Security Project (OWASP) foundation.
Supported by a global network of experts, OWASP’s Mobile Application Security initiative is a comprehensive framework comprised of three main components.
The Mobile Application Security Verification Standard (MASVS) outlines a broad set of requirements tailored for mobile software.
Complementing this, the Mobile Application Security Testing Guide (MASTG) offers detailed insights into the correct procedures, techniques, and tools essential for app security testing. For clarity and ease of use, this guide also provides illustrative test cases as practical examples.
Additionally, the mobile app security checklist, available in PDF format and multiple languages, presents a consolidated view of all MASVS requirements, aligning them with corresponding test cases from MASTG.
Ensuring mobile app security is a highly important task. That’s why it should be assigned to skilled engineers who have the required experience and testing tools.
QTS has such experts who work in well-coordinated teams and offer a wide range of mobile app development services. We perform careful, comprehensive testing and ensure the highest standards of quality and security throughout the whole development life cycle.
Contact us to get a mobile software product built according to the leading quality and security standards of the industry, including OWASP, ISO, GDPR, HIPAA, and others.



